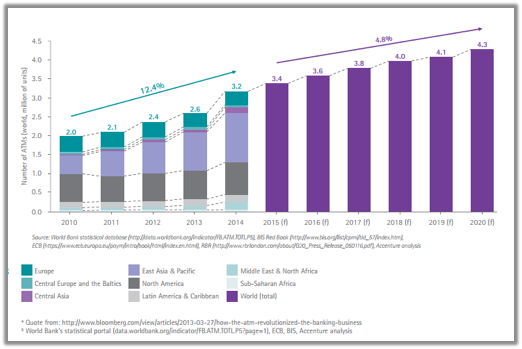
An ATM is an electronic apparatus that allows a bank’s customers to make cash withdrawals. It also provides other banking facilities 24/7/365 without human assistance. The ATM channel is still maintaining its central role as an essential banking touchpoint with consumers. It has become an integral part of a bank’s Omni-channel experience. It doesn’t only play a key role in the broader context of modern banking but also acts as a major enabler of mission critical ‘access to funds’ functionality within financial inclusion initiatives of State Bank of Pakistan. The channel is taking an even more important role as branch network optimization, eventually leading to reduction in number of branch counters by offering diversified banking service experience, while consumers still express a preference for banks with physical presence. One of the leading payment processing firms published a study highlighting the importance of ATM network expansion:
Historical Pursuit
From the historical perspective, in 1967, a Scottish inventor named John Shepherd-Barron was sitting in his bathtub. He suddenly had a flash of genius: If vending machines could dispense chocolate bars, why couldn’t they dispense cash? Barclays, a London bank, loved the idea. They installed Shepherd-Barron’s first ATM in a branch on Enfield High Street not long afterwards. Unlike modern ATMs, Shepherd-Barron’s did not use plastic cards. Instead, it used paper vouchers printed with radioactive ink so that the machine could read them. The customer entered an identification code and took cash – a maximum of £10 at a time. Like any other traditional “Gizmo” the ATM had gone through the evolutionary phase to a highly advanced state automata machine capable of processing numerous complex routines and cipher operations in tamper-proof modules that securely process transactions in secure and elegant fashion as we see today.
Security Placement
Modern ATM physical security does actually concentrate on denying the use of the cash inside machine to a thief or a fraud using some high tech industry standard fraud detection techniques. Albeit, with all the promising features that an ATM bestows, in the present day world, fraud criminals are affecting industries. And not only in terms of monetary loss but also in terms of capital and resources aimed at preventing fraud. Conventionally, ATMs typically connect directly to their ATM transaction processors. The bank establish a dedicated secure VPN to operate the ATM network in a “Star topology” fashion.
Typically, ATM machines runs on Microsoft Windows platform. However, banks can also use customized variants to deploy on Linux operating system. Speaking of transaction security that kicks off from the ATM secure tamper-proof “PIN PAD” responsible for encrypting card PIN using industry proven symmetric cryptographic algorithms, ATM security uses a fortified cash dispenser and secure card readers.
Recommendations to Counter Logical Threats
TPS has recommendations as to how companies can secure themselves. Logical attacks are becoming a major growing attack-vector, one that has the potential to cause large losses and the bad news is that with time, hackers will only get better. Considering industry-wide best practices, TPS recommends the following logical security measures to be in place to compliment the overall security of the ATM transaction processing life cycle.
Fraud Prevention Platform
Fraud poses a significant threat to industry. Banks need to make surging investments and efforts in order to address it. The need of the day is to implement world’s best fraud prevention system for preventing ATM based frauds. ATM acquirers that operate networks of ATMs have access to a massive number of so-called “Machine events”. Banks should deploy a suitable fraud management and prevention solution. The solution should be able to merge non-financial transactions to historical profiles and combine them with financial transactions for records. This can help prevent ATM based fraudulent transactions in real-time.
Dynamic CVV
Shimming refers to an attack that captures data by tapping directly into an EMV chip. A small, flat device containing a microprocessor and a flash memory card inserted inside a card reader. The circuit is energized through engagement with the chip while it’s in the card reader and the device sniffs the data. Although shimmers cannot use the data to fabricate a chip-based card, they can use it to clone a magnetic stripe card. While the data that is typically stored on the card’s magnetic stripe, it is replicated inside the chip on chip-enabled cards.
The chip contains additional security components not found on a magnetic stripe. One of those components is an integrated circuit card verification value or “iCVV”or “dCVV” for short (also known as a “Dynamic CVV”) generated at the time of transaction. The iCVV differs from the card verification value (CVV) stored on the physical magnetic stripe, and protects against the copying of magnetic-stripe data from the chip and using that data to create counterfeit magnetic stripe cards. The one of ways for an attack to be successful is if a bank card issuer neglects checking the iCVV & POS Entry conditions sent with each transaction. These conditions provide the issuer with necessary information on how the merchant or the ATM acquired transaction data when authorizing the transaction.
Asymmetric Cryptography
ATM Network operators (acquirers) should opt for encrypting “Point to Point” communication channels with additional RSA based asymmetric cryptography using Transport Layer Security (TLS 1.3 standards) along with secure hashing aka MAC-ing. This approach can prevent data leaks from replay & host ghosting attacks.
Remote Rotation of ATM Master Key
Remote rotation of ATM Master Key responsible for encrypting PIN, helps banks ensure that if symmetric keys are compromised, they become useless as master keys are regularly substituted. This also helps in replacing the dual operator or split knowledge implementation of keys on each ATM since it securely automates the whole procedure without any human intervention.
Two-Factor Biometric Authentication
Along with EMV based transaction processing, two-factor biometric verification can help secure the transactions. In two-factor authentication, ATM processor/controller invokes dynamic and randomized 1-10 fingerprint authentication flows.
Recommendation to counter Physical Threats
TPS strongly recommends that all ATM operators deploy anti-fraudulent systems as part of an overall layered approach to ATM security as the saying goes “Every Little Thing It Does Is Magic.” Consider the following:
- Anti-skimming detection sensors to detect card reader intrusions and stereo skimming attacks
- Anti-card trapping detection sensors with automated alarm broadcasting to ATM processor to make the ATM machine “Out Of Service” instantly.
- ATM fascia and cabinet alarms integrated online with ATM controllers for transaction monitoring data centers and disabling ATM on real time basis.
- PIN pad shields/guards to prevent PIN prying attempts via Pinhole cameras.
- CCTV coverage and not just relying on ATM image capturing solutions which may become incapacitated in case of “Ghost in the Machine” [Malware] scenario.
- Keep a close eye on your bank statements, and dispute any unauthorized charges or withdrawals immediately before the customer dispute soliciting window officially expires.
- Don’t believe in the hoaxes. Keying in your PIN backwards at an ATM will not call the police. These are simply scams to get you to divulge your PIN.
An Interesting Story
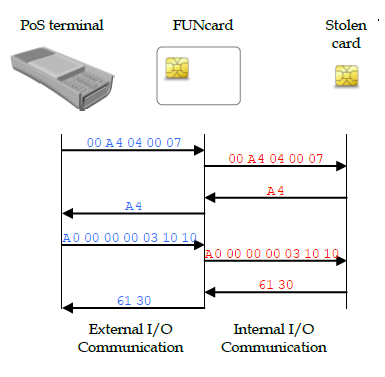
Five years ago in France, criminals stole about a dozen credit cards equipped with chip-and-PIN technology. In May 2011, a banking group noticed that criminals were using those stolen cards in Belgium. This should have been impossible without the card holders inputting their PINs. That’s when the police got involved. The police obtained the International Mobile Subscriber Identity (IMSI) numbers to track locations where the cards were being used. They also traced their times of usage, and then they correlated those IMSI numbers to SIM cards. Police seized 25 stolen cards, specialized equipment, and $5,660 in cash. The police ultimately stated that the stolen amount was approximately $680,000, involving 7,000 transactions and 40 cards.
The research explained that a typical EMV transaction involved three steps: card authentication, cardholder verification, and then transaction authorization. In the altered cards, the original chip was allowed to respond with card authentication as normal. Then, during card holder authentication, the POS system would ask for a user’s PIN. The thief would respond with any PIN, and the FUN card would step in and send POS, the code indicating that it is okay to proceed with the transaction because the PIN is checked out. During the final transaction authentication phase, the FUN card would relay the transaction data between the POS and the original chip, sending the issuing bank an authorization request cryptogram tells the POS system if the transaction has to be accepted or not.
Aftermath & Lessons Learned
The forensic report produced by the authors of this paper was sufficient for the court to condemn the perpetrators. They underlined to the court that this case shows organized crime is very attentively following advances in information security. We also noted that producing the forgery required patience, skill and craftsmanship. It is important to underline that the attack described in this paper is not applicable anymore. Thanks to the activation of the new authentication mode: Combined Data Authentication (CDA). Besides CDA, network level protections act as a second line of defense. Until the deployment of CDA, this fraud was stopped using network-level counter-measures and POS & ATM software updates. We cannot detail the network-level countermeasures for confidentiality reasons”.
This case illustrates that a nonmalleable cryptographic secure channel must always exist between cards and readers. Other (more expensive) solutions allowing to avoid man-in-the-middle devices consist in relying on physical attestation techniques such as (i) Parity Faults (ii) Abnormal application behavior, etc.
In Conclusion
Banks! The mantra of any good security department is: Security is a not a product, but a process. It is more than designing strong cryptography into the system; it’s designing the entire system such that all security measures, including network, cryptography, processes, and applications work together.
ATM users! Don’t let one simple transaction like withdrawing money from an ATM become a way for thieves to get to you. To avoid scams like these, listen to the warning intuitions in your head and be careful when something feels amiss.
Disclaimer: This post originally appeared in the TheNewSpaces blog.










Leave A Comment